Flare-on-07 001 - Fidler
Overview
I am playing flareon-08 righ now and i’m stuck at challenge 08 so i decided to play flareon-07 challenges until i come up with something.Meanwhile, i can sharp my weapon even more better playing these ctfs.
Challenge info
Welcome to the Seventh Flare-On Challenge!
This is a simple game. Win it by any means necessary and the victory screen will reveal the flag.
Enter the flag here on this site to score and move on to the next level.
This challenge is written in Python and is distributed as a runnable EXE and matching source code
for your convenience. You can run the source code directly on any Python platform with PyGame if
you would prefer.
Solving Challenge
When we run the program, it asks for the program to begin with.
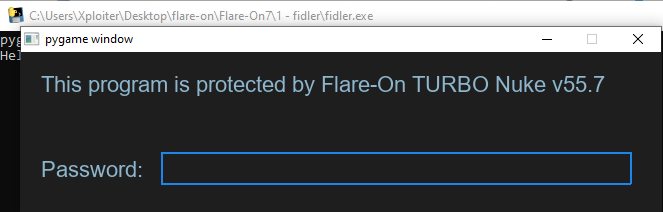
If we look into the source code we can see that the password_screen() function is responsible for showing the password screen. Inside the function in while loop if the input is given it’ll call password_check(input_box.text) function and returns true if the password_check function returns True else it’ll return False.
def password_screen():
screen = pg.display.set_mode((640, 160))
clock = pg.time.Clock()
heading = Label(20, 20, 'This program is protected by Flare-On TURBO Nuke v55.7')
prompt = Label(20, 105, 'Password:')
input_box = InputBox(140, 100, 470, 32)
controls = [heading, prompt, input_box]
done = False
input_box.active = True
while not done:
# [...]
if input_box.submitted:
if password_check(input_box.text):
return True
else:
return False
# [...]
In password_check function, we can see the altered_key variable holding string hiptu. Then in next line it loops through each characters in string (hiptu) and then it gets unicode value of each characters in loop and subtract them with 1 then the output is joined and stored in a key variable. Finally it compares the input and newly created key if they are equal it returns True else False.
def password_check(input):
altered_key = 'hiptu'
key = ''.join([chr(ord(x) - 1) for x in altered_key])
return input == key
If we see output in python shell,
>>> ak = 'hiptu'
>>> key = ''.join([chr(ord(x) - 1) for x in ak])
>>> key
'ghost'
As we can see the below code, if the password_screen() function returns True it’ll call game_screen() function else it’ll call password_fail_screen()
def main():
if password_screen():
game_screen()
else:
password_fail_screen()
pg.quit()
The game screen appears if we give the ghost as password input. Now we can see in the below image, we need to earn 100 Billion coins to win and reveal the flag. We can simply click on the cat to earn 10 coins then we can buy Autoclickers. We can keep buying the Autoclickers until it hits 100 Billion coins in few minutes.
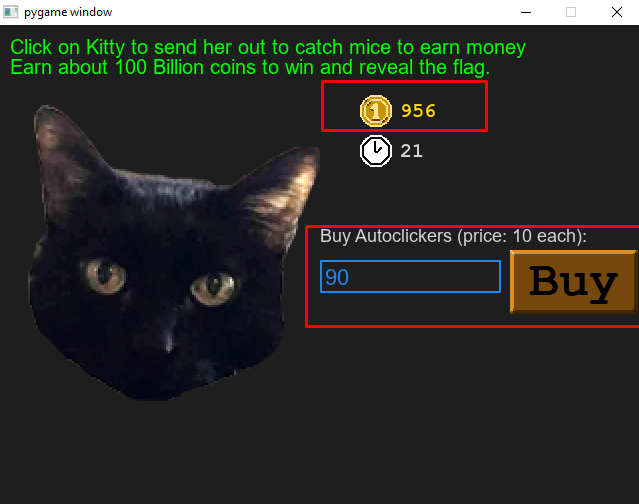
As we can see if it reaches the 100 billion it automatically shows the flag.
Now let’s analyze the code where the flag gets generated.
As we can see, if the current_coin is greater than target_ammount - 2**20 the victory_screen() function will be called. The parameter passed in victory_screen is integer value 1030.
def game_screen():
# [...]
while not done:
target_amount = (2**36) + (2**35)
if current_coins > (target_amount - 2**20):
while current_coins >= (target_amount + 2**20):
current_coins -= 2**20
victory_screen(int(current_coins / 10**8))
return
As we can confirm in the following image that the passed integer value in victory_screen function is 1030.
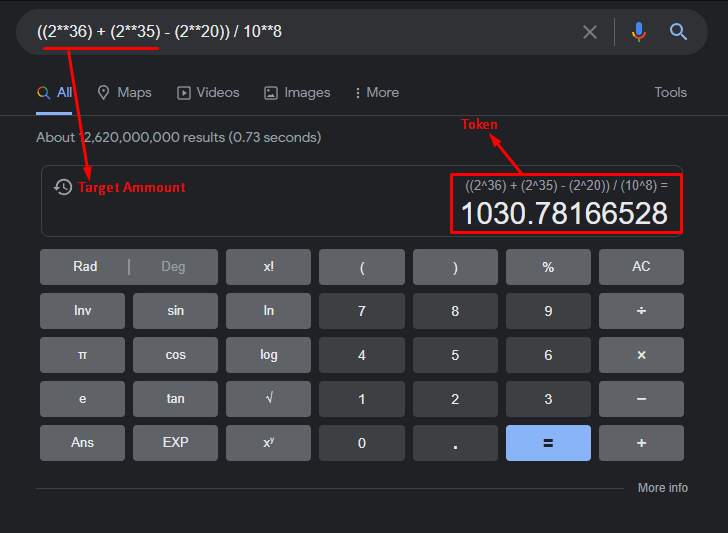
In the victory_screen function the decode_flag function is being called with token which is 1030.
def victory_screen(token):
screen = pg.display.set_mode((640, 160))
clock = pg.time.Clock()
heading = Label(20, 20, 'If the following key ends with @flare-on.com you probably won!',
color=pg.Color('gold'), font=pg.font.Font('fonts/arial.ttf', 22))
flag_label = Label(20, 105, 'Flag:', color=pg.Color('gold'), font=pg.font.Font('fonts/arial.ttf', 22))
flag_content_label = Label(120, 100, 'the_flag_goes_here',
color=pg.Color('red'), font=pg.font.Font('fonts/arial.ttf', 32))
controls = [heading, flag_label, flag_content_label]
done = False
flag_content_label.change_text(decode_flag(token))
# [...]
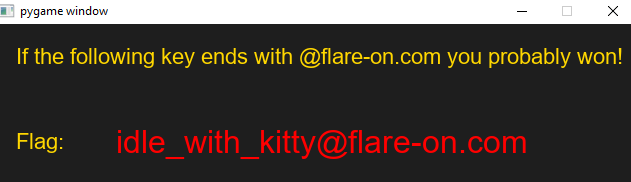
Finally all the decoding stuff is done in decode_flag function as we can see in the following image:
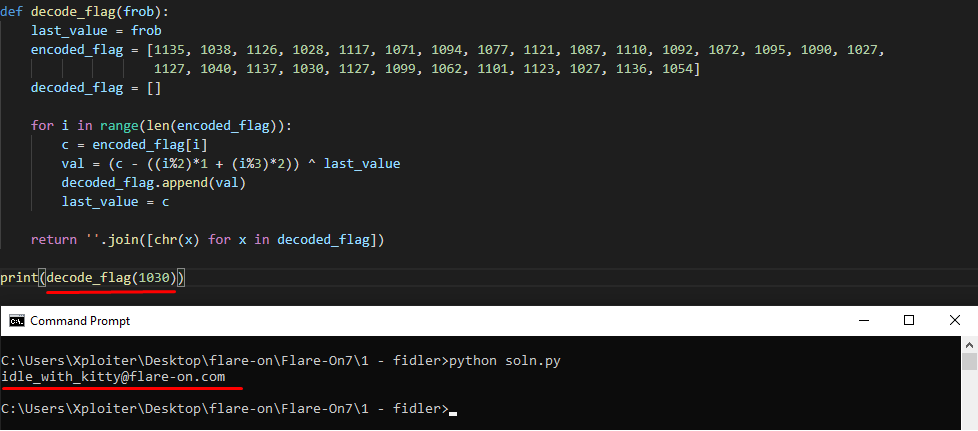
Flag
idle_with_kitty@flare-on.com